PLAY
Protect your Web Apps with TELER : HTTP Intrusion Detection as WAF with Fail2ban
Empowering Teler HTTP Intrusion Detection as WAF with Fail2ban.
What is Teler?
Teler is a free and open-source real-time HTTP intrusion detection program written in Go. It has gained popularity due to its effectiveness in detecting web-based attacks and its ease of use. Teler is designed to be used as an Intrusion Detection System (IDS), not an Intrusion Prevention System (IPS), making it an ideal solution for detecting and alerting on potential threat
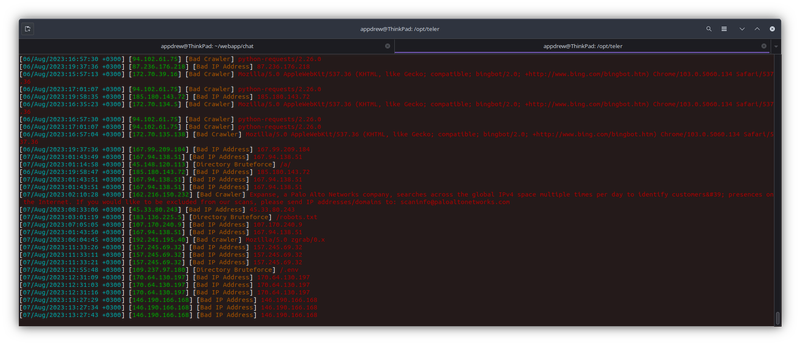
**How Does Teler Work?**
Teler analyzes incoming HTTP traffic to identify potential security threats in real-time. By leveraging its extensive ruleset, Teler can detect and alert on a wide range of web-based attacks, including SQL injection, cross-site scripting (XSS), and remote file inclusion (RFI) attacks. Its real-time intrusion detection capabilities enable swift response to emerging threats, ensuring the security of your web applications.
**Empowering Teler with Fail2ban**
To take Teler's intrusion detection capabilities to the next level, integrating it with Fail2ban can significantly enhance its effectiveness. Fail2ban is a popular intrusion prevention framework that can ban IP addresses that exhibit malicious behavior.
By combining Teler's intrusion detection with Fail2ban's prevention capabilities, you can create a robust defense system that detects and responds to threats in real-time. This integration enables automatic blocking of IP addresses that trigger Teler's rules, providing an additional layer of security for your web applications.
Benefits of Using Teler with Fail2ban
The integration of Teler with Fail2ban offers several benefits, including:
* Enhanced security: By combining intrusion detection with prevention capabilities, you can create a robust defense system that detects and responds to threats in real-time.
* Automated threat response: Automatic blocking of IP addresses that exhibit malicious behavior ensures swift response to emerging threats.
* Improved incident response: Teler's real-time intrusion detection and Fail2ban's prevention capabilities enable swift response to security incidents, reducing the risk of security breaches.
Let me know if you'd like me to revise or expand on this content!
Why Integrate Teler with Fail2ban?
Fail2ban is a popular intrusion prevention framework that can be used to ban IP addresses that show malicious behavior. By integrating Teler with Fail2ban, you can enhance your web application's security by detecting and preventing web-based attacks in real-time. This integration allows you to leverage the strengths of both tools to create a robust security solution.
**Seamless Protection Against Web-Based Threats**
The integration of Teler with Fail2ban provides an additional layer of security to your web application, enabling you to detect and respond to potential threats in real-time. By combining the advanced threat detection capabilities of Teler with the IP banning functionality of Fail2ban, you can:
* Block malicious traffic and prevent attacks before they cause harm
* Reduce the risk of downtime and data breaches
* Improve the overall security posture of your web application
**How the Integration Works**
When Teler detects a potential threat, it triggers Fail2ban to ban the IP address associated with the malicious activity.
This ensures that the attacker is blocked from accessing your web application, preventing further damage. The integration is seamless, with minimal configuration required to get started.
**Benefits of Integrating Teler with Fail2ban**
* Enhanced security posture: Leverage the strengths of both tools to create a robust security solution
* Real-time threat detection and response: Respond to attacks in real-time, minimizing the risk of damage
* Simplified security management: Integrate with your existing security infrastructure for a unified security solution
**Get Started with Teler and Fail2ban Integration**
Ready to enhance your web application's security?
Integrate Teler with Fail2ban today and experience the power of advanced threat detection and response.
Let me know if you'd like me to revise or add anything!
Setting up Teler as a WAF with Fail2ban
To set up Teler as a WAF with Fail2ban, you'll need to download the example files and configure Fail2ban to work with Teler.
Learn how to integrate Teler, a free and open-source real-time HTTP intrusion detection program, with Fail2ban to enhance your web application's security. Get a step-by-step tutorial on setting up Teler as a WAF with Fail2ban.
Downloading Example Files
Download the teler.fail2ban-filter.example.conf file, which contains the pattern for detecting web attacks:
\[<HOST>\] \[(Common Web Attack(:.*)?|CVE-[0-9]{4}-[0-9]{4,7}|Bad (IP Address|Referrer|Cra
Configuring Fail2ban
Create a new jail configuration file for Fail2ban, specifying the action to take when a match is found:
[Definition]
failregex = ^<HOST>.*Common Web Attack.*
ignoreregex =
[Init]
maxretry = 3
bantime = 600
Integrating Teler with Fail2ban
Configure Teler to output logs in a format that Fail2ban can read. Then, restart Fail2ban to apply the new configuration.
01.Requirements
Fail2ban
Teler
Linux
Web - applications / website logs
02. Usage
Benefits of Using Teler with Fail2ban
By integrating Teler with Fail2ban, you can:
- Enhance your web application's security by detecting and preventing web-based attacks in real-time
- Leverage the strengths of both tools to create a robust security solution
- Improve your incident response capabilities by detecting and alerting on potential threats
cat /webapp_path/logs/access.log | teler -c /opt/teler/teler.yaml > threads.logs
In this tutorial, we've shown you how to empower Teler HTTP intrusion detection as a WAF with Fail2ban. By following these steps, you can enhance your web application's security and improve your incident response capabilities. Remember to stay vigilant and keep your security solutions up-to-date to protect against evolving threats.
Providing assistance
The web assistant should be able to provide quick and effective solutions to the user's queries, and help them navigate the website with ease.
Personalization
The Web assistant is more then able to personalize the user's experience by understanding their preferences and behavior on the website.
Troubleshooting
The Web assistant can help users troubleshoot technical issues, such as broken links, page errors, and other technical glitches.
Please log in to gain access on Empowering Teler HTTP Intrusion Detection as WAF with Fail2ban file .
